- DORA:
DoRA
- Discover
- Offer
- Request
- Acknowledgement
-
IP:
- Class A: 0-127
- Subnet:
N:H:H:H
- Subnet:
- Class B: 128 - 192
- Subnet:
N:N:H:H
- Subnet:
- Class C: 193 - 223
- Subnet:
N:N:N:H
- Subnet:
- Class D & E: Cannot be used.
127.0.0.1: Loopback Address- APIPA: Automated Private IP Addressing
- When Router or Switch fails to give an IP the system under APIPA assumes the IP:
169.252.x.x
- When Router or Switch fails to give an IP the system under APIPA assumes the IP:
- IP address cannot be same in the same network but IP address can be same in different networks.
- IPV4: 32bit
- Have 4 classes.
- Its in numeric
- IPV6: 128bit
- Have 8 Sections
- Its in hexadecimal
- Class A: 0-127
-
MAC
- MAC is a 48bit permanent address assigned to the NIC(
Network Interface Card) assigned by the manufacturer.
- MAC is a 48bit permanent address assigned to the NIC(
-
Three Way Handshake:
- Syn: Synchronize
- Sends a Synchronize packet to start a conversation
- Syn-Ack:
- Sends a Acknowledgment to get a connection
- Ack:
- Ack to complete the connection.
- Syn: Synchronize
-
Elements of information security:
Integrity:Data Integrity ensures only authorized parties are allowed to modify the data.Confidentiality:Means only authorized person can work and see our infrastructure and digital resources.Authenticity & Availability:Authenticity is maintaining the originality while data is available.Non Repudiation:Not making a copy of the original data.
-
Security, Functionality and Usability Triangle:
-
Need For Information security:
- Confidentiality
- Integrity
- Availability
- Prevention of data-loss
- No Repudiation
- Protection
- Privacy
-
Security Threats:
- Security threats constitutes techniques and software that are potentially unsafe for the working environment for a network.
-
Attack Equation:
-
Security attack method:
Cloud Computing threats:- Threats Inside cloud security:
- Improper Access Control
- Bugs
- Data Loss
- Natural Calamities
- Misconfigurations
- Insecure API
- DOS
- Snakes / malicious insiders / spy
- Poor Security
- Threats Inside cloud security:
APT:Viruses and worms:- A malicious Program developed that replicates and attach themself to a target system.
- Spreads through user interaction.
- Worms: They are self replicating code or software
-
Mobile Threats:
- Data leakage
- Unsecured Wi-Fi
- Network spoofing
- Phishing attacks
- Spyware
- Broken Cryptography
-
Insider Attacks:
- A person within the organization is being a snake/spy.
-
Information security threats categories:
Network Threats:- Primary Components: Poor configuration of these 3 leads to intruder to exploit.
- Routers
- Switches
- Firewall
- Common Vulnerabilities:
- Default install settings
- Open access control
- Outdated software
- Weak encryption and passwords.
- Top network level threats:
- Information gathering
- Sniffing or Eves dropping
- Spoofing
- Flooding
- DNS or ARP Poisoning
- DDoS
- Session Hijacking
- MITM
- Password based attacks
- Primary Components: Poor configuration of these 3 leads to intruder to exploit.
Host Threats:- Malware attacks
- Foot-printing
- Password attacks
- Unauthorized access
- Backdoor attacks
- Privilege escalation
- Physical security threat
Application threats:Threats associated with applications or software.- Improper
- Insecure code
- Authentication and authorization
- Security misconfiguration
- Information disclosure
- Cryptographic attack
- Information leakage.
-
Types of attacks on a system:
- Exploiting vulnerabilities on a system.
Examples:- Buffer Overflow
- Unpatched Operating System
- Bugs in a Operating System
- Misconfiguration attack
- Improper setup
- Default setup
-
Application level attacks:
- Attacks done on loopholes within the application which has been unchecked
-
Shrink Wrap Code:
- Payloads or backdoor installed using compression of payloads.
-
Information Warfare:
Defensive Information warfare:- All actions taken to defend against information attacks
Offensive Information warfare:- Deny, corrupt, destroy, or exploit an adversary's information, or influence the adversary's perception
-
Hacking:
- Exploiting vulnerabilities in a system by compromising security to gain unauthorized access to a system.
-
Hacker:
- Hacker is a person who has the skill to hack.
Types of Hackers:- Black Hat
- White Hat
- Grey Hat
- Script Kiddies
- Hacktivist
- State Sponsored Hackers
- Cyber terrorist
- Suicide Hackers
-
Hacking Phases:
Reconnaissance:- Recon is the initial preparing phase by gathering information about the target.
- Types:
- Passive recon:
- Indirectly gaining information.
- Active recon:
- Directly gaining information.
- Passive recon:
Scanning by network:- Tools:
- Port scanner
- Network mapper
- Ping
- Information's included:
- Port status.
- Operating system information.
- Device type.
- Live machine
- Tools:
Gaining Access:Gaining access into the system.Maintaining access and enumeration:- By:
- Backdoors.
- Rootkits.
- Trojans
- By:
Clearing Tracks:Attacker Identity must be hidden by covering his tracks.
-
Information security controls:
- Information assurance
Maintains:- Integrity
- Confidentiality
- Authenticity
- Accessibility
- Information assurance
-
Security Policies:
Types:- Promiscuous policy: No restrictions of usage of system resources.
- Permissive policy: Restricts inly widely known dangerous attacks and behaviors'.
- Prudent policy: Ensures maximum and strongest security.
- Paranoid policy: Denies everything limiting internet usage.
-
Physical Security:
Priority:Top- All of it related to the physical system such as backups, CCTV, rf-id, and guards, etc.
-
Incident Management:
Incident Response Management:Procedure and method of handling an incident.Process:- Preparation
- Detection and Analysis
- Classification
- Notification and Announcement
- Containment
- Forensic Investigation
- Eradication and recovery
- Post incident activities
-
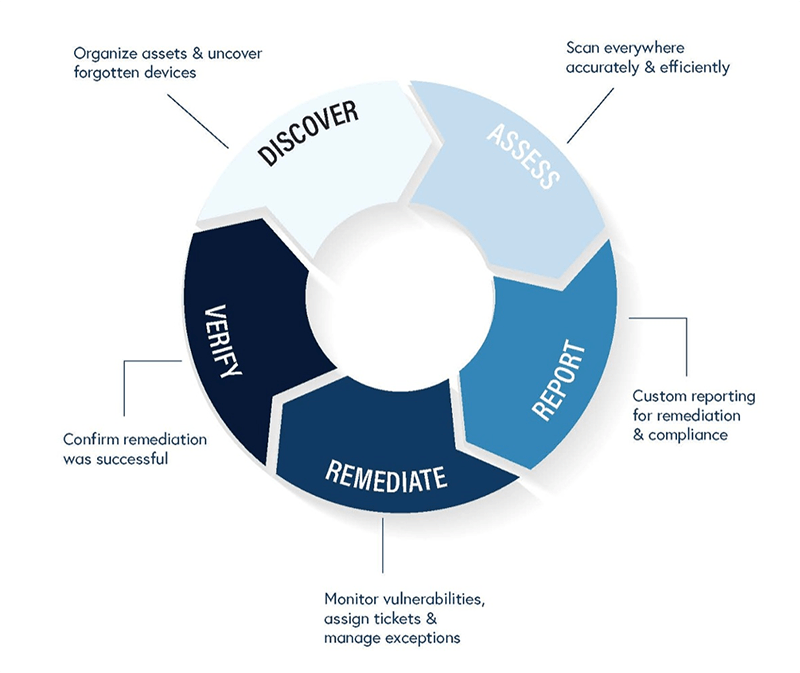
Vulnerability Assessment:
-
Penetration Testing:
- Process of hacking system with permission from the owner to evaluate security.
Types:- Black box:
- Blind Testing with no prior knowledge of the system or the target.
- Gray box:
- Limited prior knowledge of the system or the target.
- White box:
- Complete knowledge of the system and the target.
- Black box:
Phasis:- Pre-attack:
- Planning
- Preparation
- Collecting information
- Collecting security information
- Planning and designing methods for the attack
- Attack:
- Penetration
- Acquiring target
- Remediation action
- Escalation of privileges
- Post-attack:
- Securing and cleaning
- Validation
- Reporting
- Pre-attack: